When Written: Aug 2008
Testing your web site for these vulnerabilities can be very tedious, particularly if it is a large site, so what is needed is an automated way of testing a web site for such problems. Thankfully there is a very good tool available to Windows users.
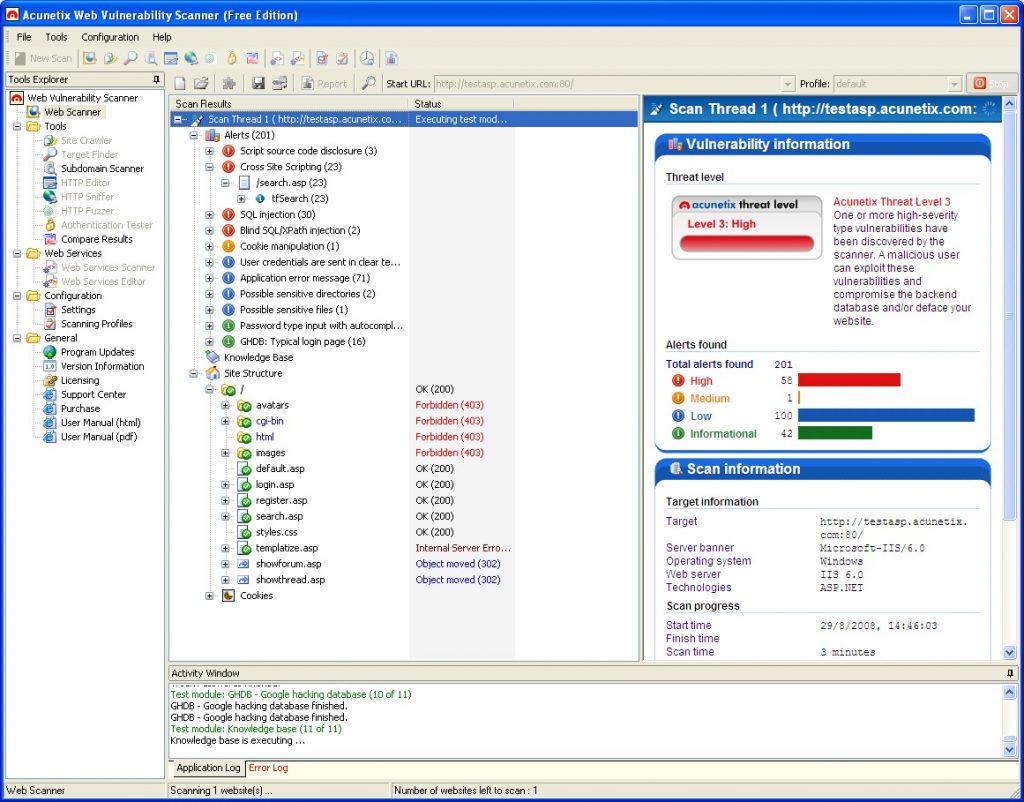
Acunetix Web Vulnerability scanner is very good but the full version is expensive
This is the Acunetix Web Vulnerability scanner (http://www.acunetix.com ), which will test for all sorts of problems. However it is quite expensive for the small developer, at $6,900 for the version that allows you to scan sites of customers. If you just want to be able to scan your own sites then you can save yourself $1,400 as it is $5,00 but either way it is a lot of money. There is free version which does allow XSS vulnerabilities to be tested for an unlimited time which is excellent news, but it will not test every web page in a site only those which seem to be linked in such a way that they appear that they might be vulnerable, so you need to be aware of this and test any pages which are missed.
Another XSS testing tool is the Open Source OWASP CAL9000 tool, which is totally free and is downloadable from http://www.digilantesecurity.com/CAL9000/ , I found this complicated to use and the UI did not display correctly in some browsers I use, but I think I was spoilt by using the Acunetix first. Acunetix is the better tool and considerably more automated, as it will trawl a web site following links and trying a range of attacks. The results are then stored in a database and you can then manually launch the attack again, which is very useful to test out any changes you have made to your web pages, saving the time it takes to do a complete scan after each modification you make.
The software also gives plenty of information about the form of the attack which helps when deciding how to code your web pages to stop it. The free license does not allow you to test web sites that do not belong to you, although an unscrupulous user could use this tool to find a vulnerably on a site, but that shouldn’t worry you should it as your site is not vulnerable, is it ?
Article by: Mark Newton
Published in: Mark Newton
